|
System Architecture




The security process in Mobile-C focuses on the secure migration process of mobile agents and ACL messages from
one agency to another.
This migration process in Mobile-C is inspired from the SSH protocol.
Before the migration process, both agencies must authenticate each other through public key authentication.
After successful authentication, the sending agency encrypts the mobile agent, calculates its hashcode and sends it to the
receiving agency.
The receiver decrypts the mobile agent, verifies its integrity and executes it.
For this security process, each Mobile-C agency must contain the following.
- Known Host File: contains the host name and public key of each agency, as an identifier, in a network.
By default, each agency trusts a known host file since it is provided by an administrator. The structure of
a known host file is shown in Figure 1.
- Public/Private Key File: each agency contains a pair of key files that are used for authentication process.
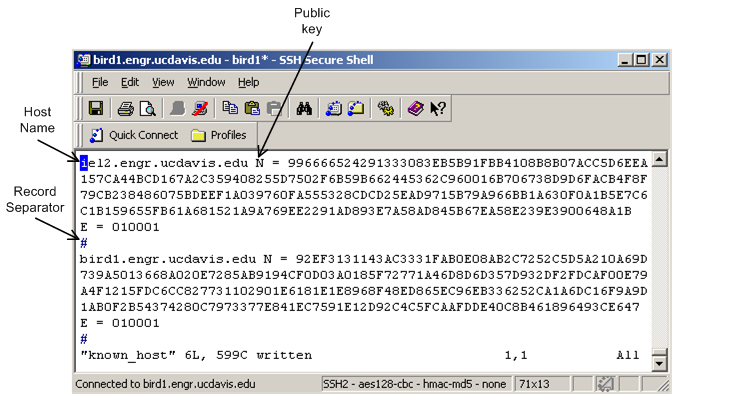 |
| Figure 1: A sample known host file |
Public Key Authentication
The cryptographic algorithm used for this process is RSA 1024 bit key size.
Each agency in a network contains a list of known hosts provided by the administrator.
This list provides RSA public keys of other trusted agencies in a network.
Before agency A transfers a mobile agent to B, A verifies that B contains a correct
private key for the public key in A's known host list.
Also, B verifies that A contains a correct private key for the public key in B's known host list.
Figure 3 shows the authentication process in details.
The authentication process is described as follows:
- Generate challenge_A: Agency A generates a 256 bit AES key, and a randomly generated 10 byte number
called nonce.
This AES key is used to en-/decrypt mobile agents or ACL messages afterwards.
- Agency A encrypts the AES key and nonce with the public key of agency B and send to B (A
gets the public key of B from its known host list). A then waits for the response from B.
- B decrypts the received encrypted text with its private key, and performs the following
- Solve challenge_A: Calculate MD5 digest of received challenge (AES key) and nonce. Increment the
received nonce.
- Generate challenge_B: It creates a 256 bit challenge for A's authentication.
- B encrypts Solved challenge_A and Generated challenge_B with A's public key
and send to A.
- A calculates MD5 digest of challenge text and nonce (challenge_A). It decrypts the received encrypted
text with its private key, and does the following.
- Verify challenge_A: Compares the MD5 digest and nonce (self calculated and received from B).
It sets the verification status to 'Ok' if matches otherwise 'Not Ok'.
- Solve challenge_B: If Verify challenge_A is successful, it calculates MD5 digest of received
256 bit challenge and nonce (challenge_B) and increments the nonce.
- A encrypts verification status and solve challenge_B with B's public key and sends to
B.
- B calculates MD5 digest of challenge text and nonce (challenge_B). It decrypt the received encrypted text
with its private key and does the following.
- Verify challenge_B: Compares the MD5 digest and nonce (self calculated and received from A). It sets
the verification status to 'Ok' if matches otherwise 'Not Ok'.
- Send verification_status to A.
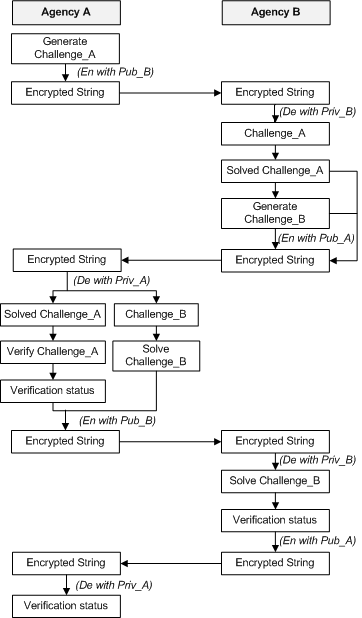 |
| Figure 2: Authentication Process |
| En. - Encryption De. - Decryption |
| Pub_B. - Public key of B Priv_B. - private key of B |
Secure Transfer
Mobile-C uses AES 256 bit key to encrypt the mobile agent at sending agency and decrypt it
at receiver side.
The insurance of security of this process rely on a secure transfer of AES 256 bit key.
Public key en-/decryption are used to transfer AES key securely.
AES key is exchanged between two agencies during authentication process.
This eliminates the further exchange of messages between two agencies for the AES key transfer.
After successful authentication, the sender agency encrypts the mobile agent with the AES key and receiver can decrypt it.
Mobile-C uses SHA2 hash code to check the integrity of mobile agents and ACL messaages.
Figure 3 shows a process of secure transfer of mobile agent from agency A to agency B.
At the end, it shows an integrity check in which agency B compares two hash codes.
If the hash code does not match, agency B tells agency A through verification code and mobile agent
would be transferred again.
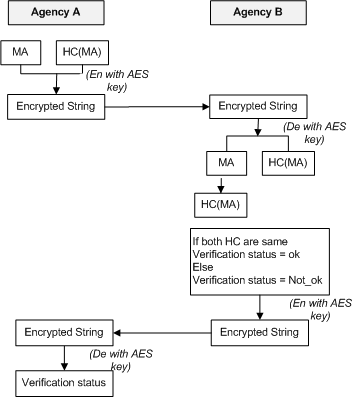 |
| Figure 3: Secure migration process |
| HC. - Hash code |
| AES. - AES key is already exchanged in Authentication Process |
|







 The security process in Mobile-C focuses on the secure migration process of mobile agents and ACL messages from
one agency to another.
This migration process in Mobile-C is inspired from the SSH protocol.
Before the migration process, both agencies must authenticate each other through public key authentication.
After successful authentication, the sending agency encrypts the mobile agent, calculates its hashcode and sends it to the
receiving agency.
The receiver decrypts the mobile agent, verifies its integrity and executes it.
For this security process, each Mobile-C agency must contain the following.
The security process in Mobile-C focuses on the secure migration process of mobile agents and ACL messages from
one agency to another.
This migration process in Mobile-C is inspired from the SSH protocol.
Before the migration process, both agencies must authenticate each other through public key authentication.
After successful authentication, the sending agency encrypts the mobile agent, calculates its hashcode and sends it to the
receiving agency.
The receiver decrypts the mobile agent, verifies its integrity and executes it.
For this security process, each Mobile-C agency must contain the following.